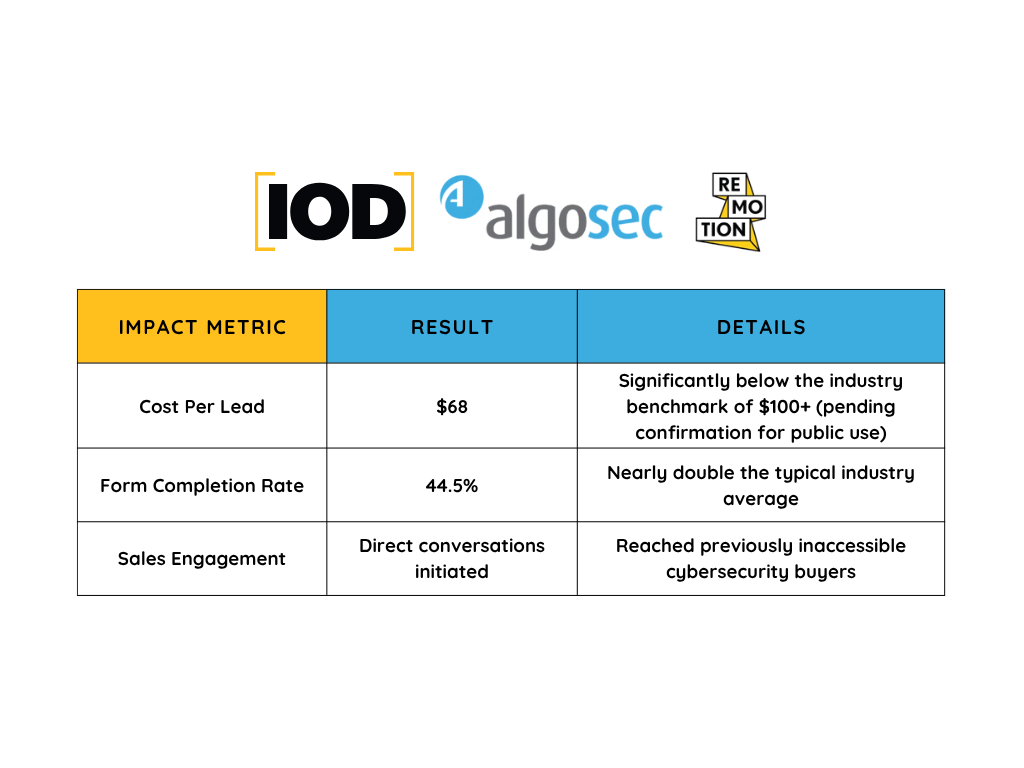
Back In 2011, during the early years of AWS, I delved into AWS cloud security, learning about the fundamental building blocks like security groups, VPC, and IAM—the very tools millions rely on today. Over the years, I’ve also revisited the AWS shared responsibility model, which has become the industry standard for cloud providers. I’ve even written blogs on these topics for AWS, which was looking to present these concepts in a way that would balance user education with responsible service adoption.
Today, AWS is ubiquitous, and security is no longer a roadblock but an enabler for cloud migration and adoption among enterprises. But cloud security is in the midst of a sea change as the cloud stack becomes more complex than ever. What worked yesterday will not work today. And a new world requires new tools and approaches.
Some key trends that have a bearing on security are the shift to multicloud, the industry-wide adoption of Kubernetes, innumerable data silos, and the rise of open source. Along with these shifting sands, the security landscape has adapted to reinvent itself by finding new approaches to security in the cloud.
In this article, I explore five key trends in this new age of cloud computing, pointing out helpful tools and solutions for each.
[NOTE: This is especially relevant with RSAC 2024 taking place this week, which IOD is attending.
If you’re in San Francisco for the conference, we’d love to connect, whether you’re an existing client or a tech vendor seeking to expand your reach in the world of cloud and infrastructure security.]
1. Zero Trust
The idea of zero trust is to never trust, and always verify users and access. This means there are no “secure” subnets and VLANs in your organization when accessed by employees.
For example, instead of just relying on user credentials, you can improve this by authenticating the user’s laptop by validating the client certificate.
One AWS blog post talks about zero-trust security as enabling “greater usability and flexibility” without compromising security. This is possible by taking a blended approach using both network-centric and identity-centric tools.
Zero trust can only work by combining authentication, authorization, and continuous verification. Note: Verifying and validating user or machine behavior should go beyond networks or devices.
This is no mean feat. It requires tooling that can scan large amounts of data and spot suspicious patterns in real time.
2. CSPM
The security posture of an organization entails the strength of its defenses and its ability to prevent or resist an external attack. The lower the chance of an attack, the better.
In the context of the cloud, cloud security posture management (CSPM) is about maintaining a strong security posture across your entire cloud presence, especially given today’s multicloud model.
The three areas of the cloud responsible for security posture are:
- Configuration
- Access
- Data
Configuration is becoming more abstracted and automated in a world where YAML sprawl abounds.
Some tools like Helm Charts or CloudFormation help save time, but shortcuts can lead to unexpected delays and issues, which are often security-related. All in all, configuration is still rife with security challenges. One misconfiguration can quickly be replicated across multiple YAML files downstream—a concern that needs to be detected and remediated quickly.
Data security is a topic worthy of a separate article itself. For now, let’s just be very brief by saying that it takes a lot to secure all of an organization’s data end to end.
A company’s data is often siloed, with different stakeholders, multiple technologies, and applications accessing it. Then there’s the challenge of securing data at rest and in transit across all the different applications and services running. Not doing this puts customer data at risk and can cause long-lasting damage to an organization’s reputation.
Amazon GuardDuty offers some help in terms of threat detection. But it takes a dedicated CSPM solution to tie all these approaches together and enable a robust cloud security posture.
3. IAM
Every cloud vendor, whether AWS, Azure, or GCP, has an identity & access management (IAM) service that controls cloud authentication and authorization for all other cloud services across the platform. The IAM service manages access for both human and non-human identities.
Below, I cover just a sample of the features AWS IAM includes:
- IAM policies define granular permissions for users to access resources like S3 buckets.
- IAM Access Analyzer enables the principle of least privilege.
- IAM roles grant both internal and external users access to your AWS resources; they also enforce multifactor authentication (MFA), essential for access security.
As you can see, IAM acts as a central hub when it comes to security in the cloud. You may only be using the very basic functions of IAM to give access to users and applications. However, it pays to understand all the capabilities of your cloud vendor’s IAM service.
In my opinion, hybrid and on-premises are a thing of the past. Still, cloud vendors want to support some of their largest clients who are still grappling with cloud migration, as—for better or worse—those clients still manage sizable on-premises infrastructure. One cloud service that helps with this is AWS IAM Roles Anywhere. It lets you configure access to non-AWS resources residing in your organization’s data center.
Going beyond IAM for your backend infrastructure, let’s say you need to manage customer access to frontend SaaS applications. Amazon Cognito is extremely scalable for managing access across web and mobile devices.
Keeping tight control over access—and having deep visibility into its usage—is essential for cloud security. IAM services from cloud vendors are a key part of enabling security for users and workloads at scale.
4. Data Protection
Numerous data breaches have occurred because of an externally accessible S3 bucket. The April 2024 Sisense breach is top of mind. Malicious actors gained access to Sisense’s GitLab code repository, which contained a token or credential providing access to the company’s Amazon S3 buckets. The attackers managed to copy and steal terabytes of customer data—email passwords, millions of access tokens, and SSL certificates.
AWS is aware of the risk and has built Amazon Macie, a scanning service that scours the length and breadth of your S3 storage buckets to identify security misconfigurations. It even helps classify all your sensitive data in a visual map.
For large organizations dealing with data across multiple AWS accounts, AWS Control Tower is indispensable. It simplifies the complex task of cloud ops—setting up, configuring, and maintaining data compliance across AWS accounts. Its ability to bake in strong security configuration around data is particularly relevant today.
In a multicloud world, organizations have data spread across more than one public cloud platform. AWS may be your primary cloud platform where you run most of your cloud workloads, but you could also be using Google Cloud for its ML and AI prowess, while your organization has always managed IAM using Azure Active Directory.
In these cases, you need data protection that can scale multicloud environments. Amazon Security Lake is purpose-built for this. In a similar vein, Microsoft Defender for Cloud offers security for data across Azure and beyond.
Every organization’s data story is unique. Selecting the right tool to encrypt and protect your data will depend on what your organization’s data looks like, how many cloud platforms it resides in, and more.
[Note to self: Start working on the next post about data security in the cloud! 🤓]
5. Cloud-Native Protection
This last trend is especially important for organizations that have already made the shift to adopt containers and Kubernetes—which should be most of you reading this. Here, we look beyond the public cloud vendors to the broader CNCF ecosystem, which supports open-source tools built around Kubernetes.
Note: Kubernetes is built to manage containers at scale, but doesn’t come with security defaults built-in. It requires you to choose and configure tools for this purpose. Fortunately, there are a host of tools for the job:
- Graduated projects: Falco, Open Policy Agent (OPA), The Update Framework (TUF), and Cilium
- Incubating projects: cert-manager, in-toto, KeyCloak, Kyverno, Notary
From this list, you’re bound to find something for multiple security use cases whether it’s defining security policies at scale with OPA, performing threat detection in real time with Falco, or taking the eBPF route to network security using Cilium.
It’s no secret that Day 2 operations can be a nightmare with Kubernetes, but selecting the right open-source tooling can make a big difference.
When looking for something as specific as a Kubernetes security solution, do consider a CNAPP solution that is purpose-built for the job. General-purpose CNAPP platforms may have a larger list of features, but they only increase the noise in the data. What you want is to separate the signal from the noise, and purpose-built CNAPP solutions are the way to go.
“If software is eating the world, open source is eating the software world” today. And the CNCF serves as the hub of this innovation by providing a platform for the most innovative open-source projects to have a place to live and breathe. The best part is that CNCF projects are vendor supported in most cases.
That’s right, outright rivals like AWS, Azure, and Google Cloud would dedicate their employees’ time to work on the same projects under the CNCF umbrella.
This is a thing of beauty and a much-needed change from the past infighting within the cloud ecosystem. Open source may have been the bane of software security yesterday, but today, cloud-native security is not possible without open-source tools. How things change in the cloud in just a few years.
Final Notes
These five pillars I covered do overlap somewhat. For example, access management features prominently in the first three, while the concept of policies weaves its way through multiple security best practices discussed. The importance of data security is evident in both CSPM and data encryption.
Hopefully, together they all give you a good sense of what to work towards as you craft your organization’s cloud security practices. Here’s to a safer future in the cloud.
Looking to produce cloud security content at scale? Join the likes of Microsoft, Check Point, Wiz, and other industry leaders. Get in touch with IOD today.
Or, come meet us at RSAC 2024. Schedule a meeting.