Cybertech Global TLV 2022 brought the world’s most advanced security companies to Tel Aviv, and I was excited to attend for the first time in person. I spent my time cruising among the different booths, learning about today’s most innovative cybersecurity companies.
While I had fun collecting the best swag at the show, I also got to meet company representatives who shared their knowledge about the latest tech.
This recap explores the top eight cybersecurity solutions that were on display.

With an oceanic theme, Orca Security took Cybertech attendees on a deep dive into their technology. Despite the large crowd, Orca’s reps took time to show me their sophisticated platform, which helps clients improve their cloud security posture.
Underneath the clean simple interface is an ocean of automation, customization, and context-aware security that surfaces the most critical issues from each cloud platform. Orca has a rapidly growing list of clients that value a quick, context-aware, and comprehensive approach to cybersecurity.

About the Company
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents. (Source: Orca Security)



One of the most well-established tech businesses at the event, Synopsys had a lot of knowledge about security to share. At their booth, Sales Engineer, Erez Noam, walked me through the very thorough process Synopsys uses for security software—starting at the silicon layer.
Synopsys has a unique set of offerings to manage supply chain risk, keeping the software development process secure from start to finish. That might be why the company has been a Gartner Magic Quadrant leader in application security testing for the past five years.
About the Company
Synopsys technology is at the heart of innovations that are changing the way we live and work. The Internet of Things. Autonomous cars. Wearables. Smart medical devices. Secure financial services. Machine learning and computer vision. These breakthroughs are ushering in the era of Smart, Secure Everything―where devices are getting smarter, everything’s connected, and everything must be secure. (Source: Synopsys)
Our Posts: Women in Tech Interviews
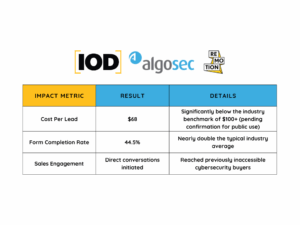
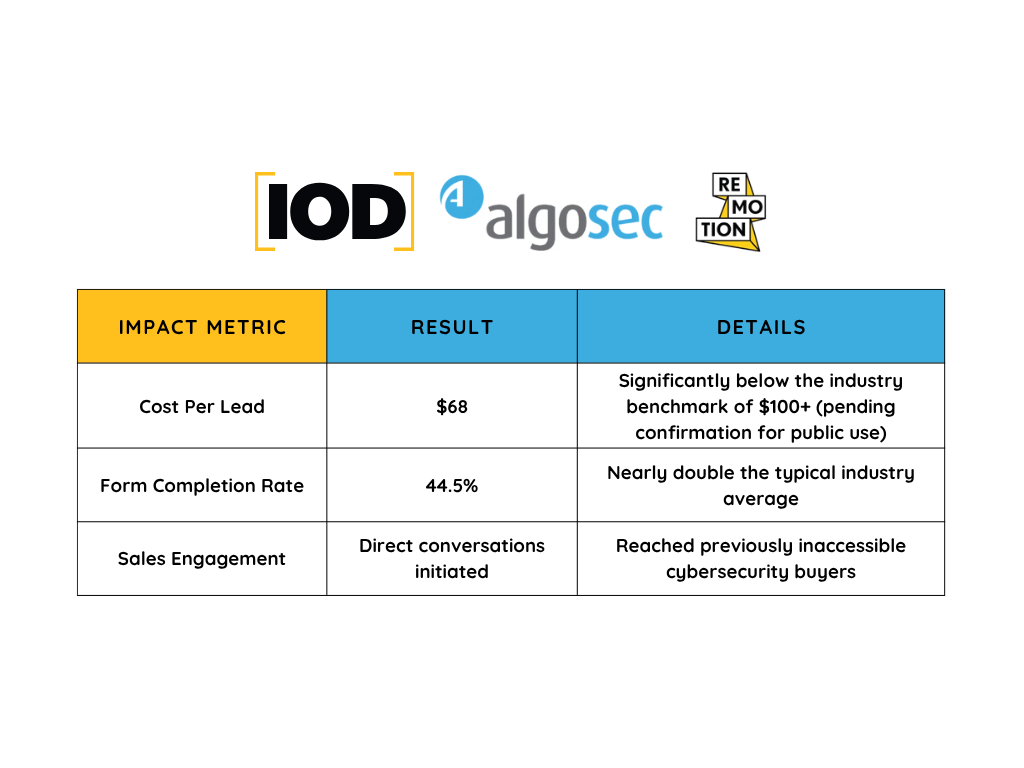
How IOD-Remotion Helped AlgoSec Slash CPL by 30% and Double Lead Quality on LinkedIn
LinkedIn has become the key channel for engaging B2B tech buyers. But reaching your audience isn’t easy. It takes proficient, practitioner-led content combined with smart
Choosing Responsible AI: Comparing LLM Providers on Ethics, Transparency, Safety, and Compliance
In 2018, Amazon created an internal AI engine to find the best job applicants. But they were forced to scrap it right away. The problem?
Amazon Nova Act and the New AI Agent Space: What Enterprises Must Know
Amazon Nova Act isn’t just another toy—it’s a bold move into the emerging world of agentic AI. It signals Amazon’s bet on what comes after

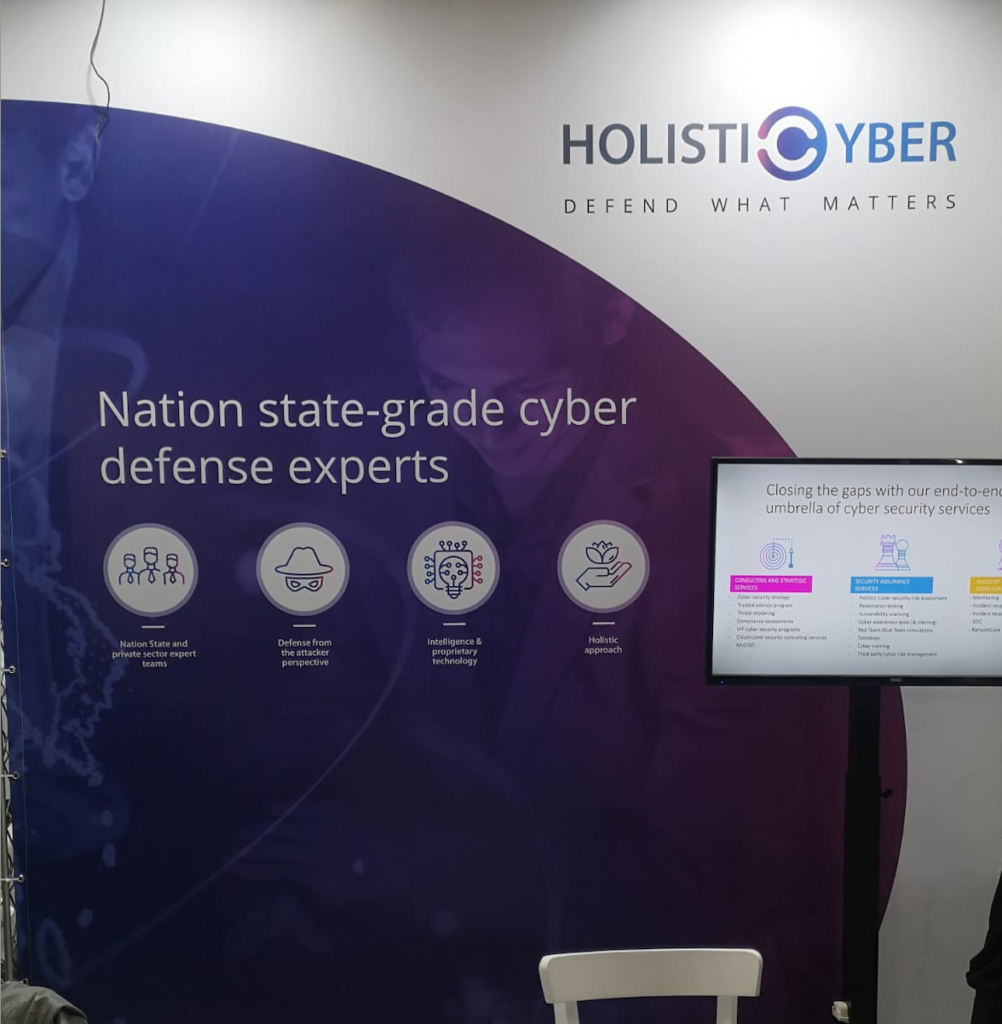
Nation-state threats are a serious concern these days, and HolistiCyber knows exactly how to handle cyberthreats at that level. Their consulting services and solutions are led by a team of IDF-trained cybersecurity veterans.
I visited the HolistiCyber stand to see what it’s like to have nation-state-grade cyberdefense on your side. The booth was brimming with activity when I arrived. Hava Katz, Product Marketing Manager, walked me through the company’s cyberdefense methodology, including its sophisticated assessment, training, simulation, and analysis capabilities.
About the Company
HolistiCyber’s mission is to assist corporations in defending themselves from the new phase of evolution in Cyber threats – not only in volume, but in the level of sophistication. Hackers, backed by Nation-States, in many cases, use tools that were developed by the NSA and other Nation-State agencies that have leaked into the Darknet. HolistiCyber’s holistic approach includes a comprehensive understanding of business processes and identification of organizations’ critical and strategic assets – all from the view point of potential highly sophisticated attackers. (Source: HolistiCyber)
The Ultimate AWS re:Invent 2021 Expo Floor Recap

Next, I visited the lively Perimeter 81 booth, with its distinctive colors and cryptic lettering style. Sales Executive, Tal Avrahami, described Perimeter 81’s modern “Cybersecurity Experience” platform. The company has embraced a cloud-forward remote approach to work and has developed some of the most impressive Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) technology on the market.

About the Company
Perimeter 81 radically simplifies cybersecurity with the world’s first Cybersecurity Experience (CSX) Platform. As a holistic, cloud-based solution, Perimeter 81 allows organizations of all industries and sizes to support the immediate desires of the nomads with a purpose—while still granting IT teams the ability to manage it all safely. (Source: Perimeter 81)





Despite the company’s name, Illusive was not elusive to find! Their distinctive purple stand framed an energetic scene. Hila Ohana, Illusive’s Product Manager, expertly walked visitors through the company’s identity risk-management platform. Illusive defends its customers against ransomware and targeted identity-based attacks by continuously scanning endpoints for vulnerabilities and automatically mitigating them, based on client policy. Seeing the product in action, I quickly understood why Illusive’s clients have a 100% win rate against red-team testers.
About the Company
Illusive protects customers against the attack vector exploited in all recent ransomware and targeted cyber attacks by continuously discovering and automatically mitigating privileged identity risk. Illusive provides security teams with the visibility they need to prioritize risk mitigation efforts, enable zero trust initiatives, and avoid ransomware, red-team embarrassments, and audit findings. (Source: Illusive)


Next, I made my way to one of the largest booths at the event: CyberArk. There was a dynamic crowd around the booth, and it wasn’t just because of the swag. CyberArk Chairman and CEO, Udi Mokady, delivered Cybertech’s keynote address: “Identity Security and Attacker Innovation.”
At the booth, I met CyberArk’s Security Services Manager, Teimyr Mamedov, who was giving demos of their identity security platform. CyberArk Blueprint locks down privileged access management so successfully that the company has stayed at the top of the Gartner Magic Quadrant for three years running.
About the Company
CyberArk is the global leader in Identity Security. Centered on privileged access management, CyberArk provides the most comprehensive security offering for any identity – human or machine – across business applications, distributed workforces, hybrid cloud workloads and throughout the DevOps lifecycle. The world’s leading organizations trust CyberArk to help secure their most critical assets. (Source: CyberArk)

When I visited Multipoint Group, I found a busy crowd asking about SealPath. To clarify, SealPath, which specializes in corporate data protection, has expanded its distribution agreement with MultiPoint Group, a value-added distributor from Israel with expertise in cybersecurity and IT solutions.

At the MultiPoint Group booth, Sandrine Roux-Campagne, Information Rights Management Lead, took me through a demo. The platform delivers Information Rights Management (IRM) protection for companies that need to safeguard information in a wide range of formats. More than 250 customers already use SealPath to protect hundreds of thousands of critical documents every month.
About the Company
Data is the fuel that powers today’s businesses. It can be used to make decisions, drive operational excellence, leverage trends, and inform strategy. Data makes enterprises run smarter, faster, and better. At SealPath, we believe there is a paradigmatic shift in handling and protecting business information. In an increasingly connected world where data is becoming more mobile, the means to protect it should keep up the pace without generating business disruption. (Source: Sealpath)

I enjoyed finding our friends at Akeyless on the expo floor—their stand was busy and vibrant! Akeyless is a top secrets-management vault provider that has grown rapidly in recent years. With my awesome swag (a USB mug warmer and coffee cup) and a nice glass of wine in hand, I was ready to watch Jeremy Hess, Head of DevRel, showcase the suite of features that make Akeyless such a valued partner for DevOps teams.

About the Company
Akeyless provides an innovative Secrets Orchestration Platform that successfully unifies several related use cases via a single solution. It offers secrets management, zero-trust access (PAM 2.0) and data protection (encryption, signing and KMS), based on Akeyless DFC™ , the firm’s unique virtual HSM FIPS-certified technology. (Source: Akeyless)
Honorary Mentions
It was wonderful to see so many innovative companies under the same roof at Cybertech Global TLV 2022. Although I didn’t have time to visit every stand, there are a few companies that deserve honorary mentions:






Summary
My in-person visit to Cybertech Global TLV 2022 was just as exciting as I’d hoped. It was thrilling to see so many elite companies showcasing their innovative solutions. We hope you enjoyed this sampling of the exhibitors and look forward to meeting more of you in person at next year’s Cybertech!