From an attacker’s perspective, cloud providers aggregate access to many victims’ data into a single point of entry. As the cloud environments become more and more popular, they will increasingly become the focus of attacks. Some organizations think that liability can be outsourced, but no, and I hope that we all understand it cannot. The contract with your cloud vendors basically means nothing, the ISVs or should I say the `SaaS providers` still holds the responsibility, so rather than focusing on contracts and limiting liability in cloud services deals, you should focus on controls and auditability.
From an attacker’s perspective, cloud providers aggregate access to many victims’ data into a single point of entry. As the cloud environments become more and more popular, they will increasingly become the focus of attacks. Some organizations think that liability can be outsourced, but no, and I hope that we all understand it cannot. The contract with your cloud vendors basically means nothing, the ISVs or should I say the `SaaS providers` still holds the responsibility, so rather than focusing on contracts and limiting liability in cloud services deals, you should focus on controls and auditability.
“Dropbox, … deceived users about the security ..The FTC complaint charges Dropbox with telling users that their files were totally encrypted” Wired Magazine
The cloud customers from the ISV who uses Amazon AWS to the small buisness who uses online tools all the way to the end users become pretty smart hence very careful with the security of the online services which they use. The users are able today to perform basic security examinations to the system such as checking the quality of the SSL encryption or even executing enhanced test of systems security’s roots that are done by the enterprise customers of the service providers.
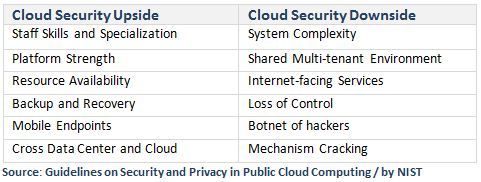
The economies of scale allow the IaaS vendor to induce specialization which allows the dedicated security team to concentrate exclusively on the security issues. The uniformity, homogeneity and the resiliency of the cloud computing facilitate platform hardening and enable better automation of security and disaster recovery procedures.
ISVs and IT organizations that deliver web applications on any end point devices such as smart phones and tablets actually concentrate all the data in the cloud and by that protect the data of stolen and lost devices.
Mark Bregman, CTO of Symantec points on five important guidelines enterprises should consider as they reshape IT policy to enable mobile devices to function seamlessly and securely in the cloud.
Together with the benefits, we can point on the cloud’s weakness points such as system complexities build from shared multitenant layers and it is a fact that hackers know where that data stored exactly. With cloud computing, a task that can take several days to run on a single computer will take only minutes to accomplish on a cluster of hundreds virtual machines. Because cryptography is used widely in authentication, data confidentiality and integrity, and other security mechanisms, these mechanisms become, in effect, less effective with the availability of cryptographic key cracking cloud services. Such case happened this year when servers owned by Amazon were used as a staging area for the hack that crippled Sony’s online entertainment network, according to a source quoted by Bloomberg.
Key Security and Privacy Issues
No doubt that the biggest obstacle these days in the cloud computing market is security. Once security breaches are discovered an immediate and a severe negative impact on the service reliability will take place hence on the ISV business. The following list presented in the NIST report highlight privacy and security related issues that are believed to have long-term significance for cloud computing.
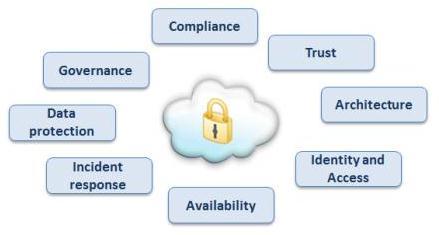
Source: Guidelines on Security and Privacy in Public Cloud Computing / by NIST
1 – Governance – Policies and procedures for privacy, security, and oversight could be overlooked and the organization put at risk. Audit mechanisms and tools should be in place to determine how data is stored, protected, and used; to validate services; and to verify policy enforcement.
2 – Compliance – Compliance involves conformance with an established specification, standard, regulation, or law. Various types of security and privacy laws and regulations exist within different countries at the national, state, and local levels, making compliance a potentially complicated issue for cloud computing. The ISV or an IT organization must scrutinize its customer’s legal requirements together with its cloud vendors’ compliance. As an exmpale for an IaaS compliance you are welcome to check the up to date Risk and Compliance (May, 2011) publish by Amazon AWS.
The most popular known are the standard ISO 27001 and the audit statementsSAS 70. There are also specific standards for government
organizations (FISMA, NARA) or specific for an industry such as HIPAA or PCI DSS.




4 – Trust – The SaaS vendor (developer) relinquishes direct control over many aspects of security hence choosing the cloud vendor should be carefully done taking in mind that the IaaS and PaaS providers have an inside system access including their employees, contractors and other parties that have received access to an organization’s networks, systems, and data to carry out operations. There must be a tight collaboration of the cloud providers in the IaaS and PaaS layers but this doesn’t mitigate responsibility of the SaaS vendor to make sure that the arrangements be disclosed in before closing the agreement with different cloud providers.
3 – Architecture – The architecture of software in the cloud comprises hardware and software. NIST report provides more details about the different layers that need to be protected:
- The `hypervisor` or the virtual machine software.
- The virtual network including software-based switches and network configurations
- Ancillary Data – cloud providers hold significant details about the subscribed accounts as well as the stored virtual machine images data.
- Application security in both client side and server side.
4 – Identity and Access Management – Data sensitivity and privacy of
information have become increasingly an area of concern for organizations and unauthorized access to information resources in the cloud is a major concern. On this matter you will find market standards such as SMAL for identify the user and XACML to control access to resources. There are today many initiatives and startups that delivers tools for access management and user provisioning for SaaS systems. One that I liked was mentioned in one of my past posts – Simplified, the company products support the enterprise with universal single sign that works across SaaS systems that serves the enterprise users.
5 – Data protection – The data isolation is one of the major security issues that are raised by potential SaaS users and customers. Data isolation basically means that a specific subscriber (user) will not be able to browse to other tenants’ data using the shared environments. Data protection includes also strict procedures when storage is moved or backups are kept. Data must be secured and encrypted while at rest, in transit or in use. Standards for communications protocols and public key certificates allow data transfers to be protected using cryptography.
6 – Availability – Always and also since Amazon failure last month, the discussion about availability valid and now it is even more intense. The level of availablity hence reliability of a cloud vendor should be examined carefully including its capabilities for backup and recovery to ensure the recovery and restoration of disrupted cloud services and operations. The SaaS vendor should also plan its own disaster recovery using alternate services, equipment, and even offshore locations. This should be planned inside its cloud using cross cloud facilities and even cross cloud vendors.
7 – Incident response -Organized method for dealing with the consequences of an attack against the security of a computer system. The cloud provider’s role is vital in performing incident response activities, including incident verification, attack analysis, containment, data collection and preservation, problem remediation, and service restoration. As in the last section for availability the SaaS vendor should also take its own security measures to protect the application layer as well include using VPC/VPN, application audits, antivirus, etc.
You are welcome to read more about that in the NIST report “Guidelines on Security and Privacy in Public Cloud Computing”, I suggest you to check the table in section 4.1 for guidelines for organizations to follow when planning, reviewing, negotiating, or initiating a public cloud service outsourcing arrangement.
What with the security of private clouds ? I managed to find an interesting article that presents the obstacles stand in front of an organization that want to have its private cloud secure and compliance with SAS70, ISO 27001 or PCI DSS. The overall conclusion self-evident, it is absurd that an organization would prefer to go through the hassle and cost of getting audited themselves in order to keep their IT in-house, when the organization could instead choose an IaaS vendor that is already have all the compliance, assurance and accreditation boxes ticked. You are welcome to check an overview of Amazon AWS security processes (May 2011) as an example of those capabilities.
To summarize, SaaS vendors (obviously for SMB and Enterprise as well) should recognize the cloud vendors’ lock-in and together with that, they should leverage the IaaS vendor capabilities, specifically the security capabilities as they should relate to them as differentiators and pure advantages in their market.
Stay tuned with `I Am OnDemand` and check part 2 next week – The Cloud Security Part 2: Vendors and Market Perceptions