By Shiji Sujai, IOD Expert
A good population of lesser mortals in this IT-dependent world start their work day by logging in to their lean, mean machines using some sort of authentication. There is an identity management solution sitting in the backend that is diligently checking your identity, and authenticates and authorizes your access before you can start your work.
Previously, before cloud arrived, this system would reside quietly in your data center, with no airs about being the single most important component of your entire enterprise application landscape. All was nice and quiet, then. However, with more and more organizations jumping on the cloud bandwagon, managing identities of users logging in from multiple devices and locations to access your cloud-hosted applications is a nightmare for any cloud administrator.
While on-premises identity management on its own is complex, adding cloud to the mix doesn’t help. With applications moving to cloud, can identity management stay behind? No, it cannot. This was the derivation of identity-as-a-service (IDaaS). Microsoft Azure offers Azure AD as a comprehensive identity management solution that helps manage identities of users on-premise, in the cloud, as well as in hybrid architectures. Let’s explore how Azure AD can address your identity management needs in a cloud-first world.
Introducing Azure AD
I have always considered identity management solutions as potential minefields where a small misconfiguration or a bad design decision can wreak havoc. You don’t realize what’s hit you until it all snowballs as potential security loopholes in your infrastructure. Azure AD tries to make your life a bit easier here. A multi-tenant identity management solution hosted in the cloud, Azure AD can be used for authentication of applications hosted in your data center, in cloud, as well as SaaS applications.
The name of the service can be misleading as it is sometimes understood to be a service offered from a Windows VM hosted in Azure with Active directory service enabled. However, Azure AD is a fully managed SaaS offering and not a replacement for the traditional Active Directory Domain Services (ADDS). While the service can be integrated with ADDS, it can also be consumed as a stand-alone identity management service by cloud-first organizations. This flexibility makes it a clear winner among competing cloud-based identity management services. It is often the first choice of enterprises with existing investments spanning multiple Microsoft technologies such as Windows servers/desktops, Microsoft Azure, and Office 365. Azure AD offers a single pane of identity management across all these technologies, as well as applications hosted in cloud.
Azure AD Features and Benefits
Leveraging Azure AD has several benefits when we consider the configuration, management, and operational aspects of an enterprise identity management system:
Ready-to-use model: As the service is hosted and managed by Microsoft Azure platform, customers do not have to worry about the backend infrastructure build, security, or high availability of the service. Instead, they can focus on integrating their applications and systems to Azure AD.
Unified access panel for applications: Users having Azure AD account can use the “My Apps” web portal, which provides a single access portal for your users to access cloud-based applications. Administrators can do tasks like user access management, password reset, and group management from the “My Apps” portal for all applications.
Improved security: Azure AD offers additional levels of security through features like Multi-factor authentication where an additional level of authentication can be enforced for secure logins. Logins also can be controlled using conditions like user device, network used for login, and roles assigned. Privileged identity management service can be used to restrict access provided to admins using the concept of “just in time” access. With “just in time,” access administrative privileges are no longer permanent, but activated when required and lasting for a predefined amount of time.
Secure collaboration: Azure AD B2C and B2B enable secure collaboration with users outside your organization. Azure AD B2C allows external users to access your corporate applications by using their social media accounts like Facebook, LinkedIn, Google+ and personal email IDs. With Azure AD B2B, users can be added as guests in Azure AD and they can use an identity of their choice to login to applications.
Flexibility of self-service: Azure AD provides flexibility for users to reset their own passwords or unlock accounts using the self-service password reset capability. Group management can also be delegated to users. This reduces the administrative overhead by eliminating SOS calls to your IT help desks for password resets.
Robust reporting: Azure AD provides a number of security and audit reports that offer insights into compromised user accounts, suspicious login activities, sign-in reports, and administrative activities. Therefore, you get a better understanding of your organization’s security posture and remediate threats proactively.
Azure AD in a Hybrid Cloud World
Having multiple identity and access management solutions for a single organization is cumbersome and can cause security loopholes to go unnoticed. Azure AD solves this problem using its hybrid identity management capability. By integrating on-premises ADDS with Azure AD, a single identity can be used for authenticating against multiple applications and resources irrespective of where they are hosted.
The Azure AD connect tool forms the heart of this architecture. It is used for synchronizing identities from on-premise active directory to Azure AD. Using the password hash sync option in Azure AD connect, the same username and password as your on-premise active directory can be synchronized to Azure AD and it can be used for logging in to cloud applications. If the authentication requests should be redirected to on-premise active directory due to security policy restrictions, either pass-through authentication, or integration with ADFS can be used. These settings are customizable and can be leveraged by organizations based on the architecture of their applications.
An additional feature that helps in this hybrid integration is Azure AD Join where Windows 10 devices can be added to the Azure AD domain. This eliminates the need for maintaining an on-premise active directory if its sole purpose is to enable user login. Azure AD domain services is another useful feature that can be enabled if a managed domain services should be made available for resources hosted in a VNet in Azure. It is specifically useful in hybrid scenarios where domain services like AD domain join or group policy can be made available for resources in a VNet without deploying a VM in the network for domain services. A sample architecture for the same is shown below.
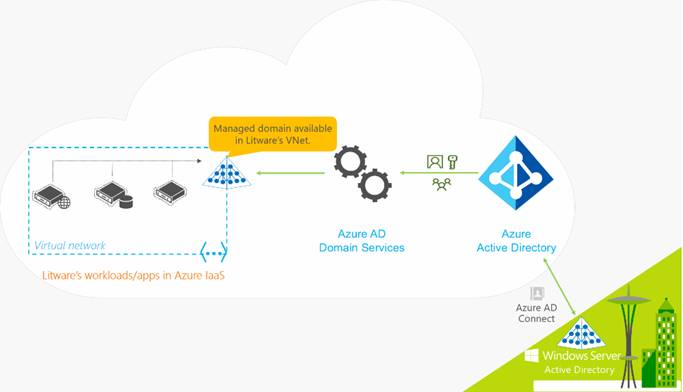
Image courtesy: Microsoft
Is Azure AD a Good Fit for my Organization?
The most important fact to be considered while adopting Azure AD is that it does not provide the familiar hierarchical structure of OUs and group policies for identity management. It is more relevant for organizations with an internet-centric approach with a diverse application portfolio and clear inclination towards BYOD / mobile work culture. User could login from any device from any place in the world. Traditional approach of redirecting authentication to a dedicated AD residing in a protected environment will not work anymore. There are many layers of security to be considered along with the configuration overheads for managing the authentication / authorization workflows within the corporate network. Azure AD precisely addresses this problem, where a secure and reliable cloud service is provided that can act as the identity service provider of the entire infrastructure.
Identity and access management continues to be a key pillar in the security architecture of all organizations, even in the era of cloud. Azure AD offers a hassle-free method of levering the capabilities of cloud to address identity requirements. The hybrid integration features boost the mass appeal of this service where having an identity system in place is never a hindrance for adoption. Single-sign on, federation, self-service user management, multi-factor authentication; there are many other cherries on this cake to pick from!
If you haven’t already, I would recommend you explore this service right away. An enterprise-class experience is guaranteed.

